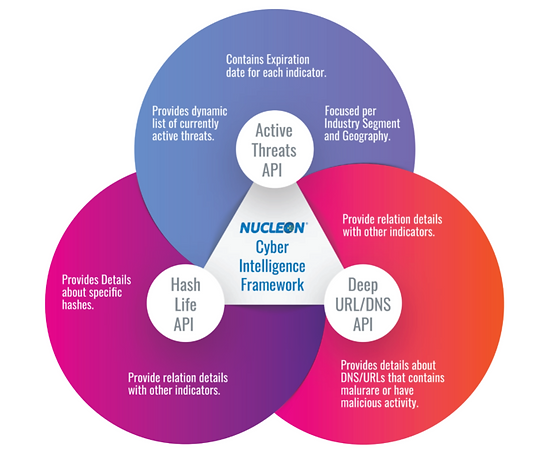
Cyber Threat Intelligence
Allow organizations of any size to proactively consume trusted actionable cyber intelligence in order to block or handle future attacks
AI Tailormade Cyber Intelligence Combinated With Deception To Protect Your Business
Cyndú's partners unique methodology includes developing cutting-edge technologies that work autonomously, locating new, never-before-seen threats. Helping you stay calm and confident about your defenses.
With decoy and deception sensors, we strike first, creating environments designed to lure the attacker in, divert the actors from your real external attack surface.
In today’s world, when information is everywhere, it’s very easy to get the wrong information. When using cyber intelligence, Nucleon’s methodology ensures that there are never any false positives.
By using our services, organizations can have their own threat intelligence team at a fraction of the cost. We help you complement your cybersecurity teams by providing them with trusted tools to handle cyber incidents and future threats.
Threat intelligence relevant to your organization – The capacity to deploy deception and decoysensors that are part of your attack surface.
Trusted threat intelligence – You control the environment and you control what, when, where and how the evidence is obtained.
Avoids alert fatigue – It’s likely that your organization is ingesting lots of false positives, our IaaS generates only information and alerts that are relevant to your organization. Saving time and effort by reducing the need to process large amounts of unnecessary data.
Strike first be proactive – With decoy and deception sensors